Note: For this demo I’m using a lab environment network that is not routed to the internet. I will be using the Ettercap open source network security tool included in the Back|Track 5 R3 Linux security distro. Before attempting to use Ettercap please make sure to read the help and MAN pages (Terminal commands shown next) for a complete description of the program options and switches.
#ettercap --help #man ettercap
To save the man page to a text file use the following command.
#man ettercap | col -b > Ettercap.txt
For this demo I will use Ettercap to search for network interface cards (NICs) that are in promiscuous mode. Having the NIC in promiscuous mode does allow Wireshark to capture all the traffic it sees on the network.
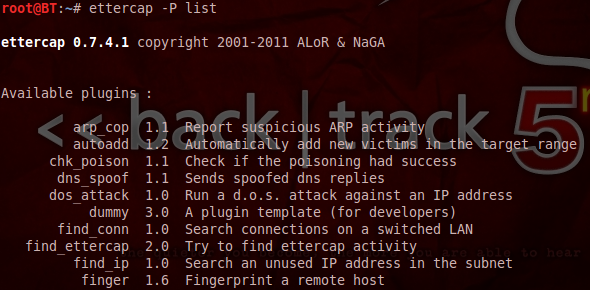
First, with the Terminal open lets run a quick command to view the available plugins for Ettercap.
#ettercap -P list
Near the bottom of the list will be the search_promisc plugin. We will use this plugin in the Ettercap command to search for the computers whose NIC are in promiscuous mode.
I will use the next command to search for the network interfaces that are in promiscuous mode.
#ettercap -T -i eth0 -P search_promisc //
Here is a quick description of the different switches used in the command.
T is for text mode only.
-i etho selects the network interface to use.
-P search _promisc uses the search promiscuous mode plugin.
// targets all machines on the subnet.
Instead of using the // switch to scan the current subnet a range of IP addresses can be specified.
#ettercap -T -i eth0 -P search_promisc /10.0.0.1-253/
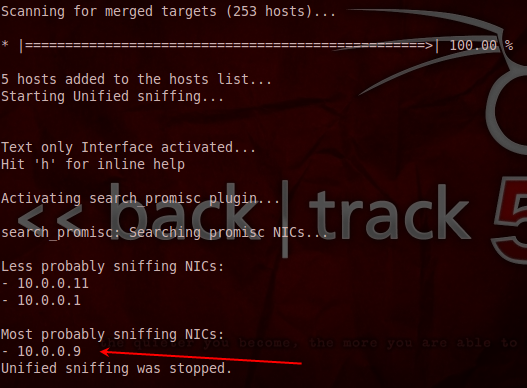
After the scan completes you will see two lists. The first list is the NICs that are not in promiscuous mode, and the second list shows the computers that are in promiscuous mode. (For the first scan I had two computers on the network and neither had their NIC in promiscuous mode)
After connecting a third computer to the network and starting Wireshark which will put the NIC in promiscuous mode I will rerun the previous Ettercap scan. This time the results will show the IP address of the computer that is running Wireshark in the probably sniffing NICs list.
If you’re not a command line person and would rather use a graphical interface Ettercap does have GUI option (see screen shot below). In my next blog post I will describe how to run this same search using the Ettercap GUI program.
Thanks for reading! If you have any comments or questions please post those below.