Note: For this demo I’m using a lab environment network that is not routed to the internet. I will be using the Fern WiFi Cracker open source wireless security tool included in the Kali Linux and Backtrack 5 r3 security distros. Before attempting to use Fern or any other utility in Kali or Backtrack please make sure to read the help and MAN pages for a complete description of the program options and switches. This demo is for wireless pentesting educational purposes and to emphasize the insecurities of using a weak or common dictionary word for wireless network authentication and encryption security key or passphrase.
Fern Wi-fi Cracker can crack WEP, WPA, and WPA2 secured wireless networks. Fern basically takes the command line utilities to crack these networks and puts them in a GUI. Very simple to use… scary easy! Fern also provides some extra functionality for hijacking sessions and locating a computers geolocation via its Mac address, but I have not tested with these features.
For this demo I will be using Backtrack 5 r3 running in VMware Workstation on a Win 7 host.
Originally I was using Fern in Kali and ran into some issues with my wireless adapter and with the program freezing or not opening after updating it. I have the fixes I discovered in another blog post for anyone else that may have these same problems.
Router Setup
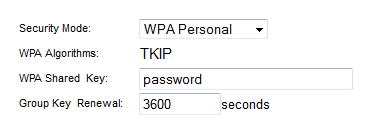
I’m using an old Cisco/Linksys 802.11g wireless router for this demo and all the settings are defaulted except the security settings, which I set to WPA Personal with a Shared Key passphrase of “password”. The word password should never be used for a real password or passphrase and I’m using it here since I know the Fern program will quickly crack it. In real world situations a WPA/WPA2 passphrase should be completely random and not a common dictionary word. For help on creating a secure WPA/WPA2 passphrase please read my earlier blog post.
Setup the Wireless Adapter
Plug in the USB wireless adapter (I’m using the Alfa AWUS036H 802.11b/g USB wireless adapter) and open the Terminal and run iwconfig to verify the USB adapter interface.
On occasions I have had to bring the wireless adapter interface up using the following command.
#ifconfig wlan0 up
Starting the Fern Program
To start Fern from the Terminal type in the following commands
#cd /pentest/wireless/fern-wifi-cracker #python execute.py
or start Fern via the GUI using the Backtrack menu
Applications/Backtrack/Exploitation Tools/Wireless Exploitation Tools/WLAN Exploitation/fern-wifi-cracker
Using the Fern Program
Select the Interface and Fern enables monitor mode. If your wireless interface does not show in the list hit the Refresh button and try again.
Before starting the scan double-click on any blank area of the Fern home screen to bring up the Access Point Scan Preferences screen. You can set the channel option to scan a single channel or leave it at the default All Channels. One nice feature is to check the Enable XTerms option which will have Fern open up the Terminal windows during its usage to see what the program is doing in the background. Click OK when done.
Back on the Fern home screen click the Scan for Access points button.
Two Terminal windows will open; one showing the WEP enabled networks (no screen shot), and another showing the WPA enabled networks. The top part of the WPA Scan Terminal window shows the networks being found, and the lower part shows any connected client devices. For a WPA attack to work it requires a connected client. The most important part of the attack will kick the client off the wireless network and capture the 4-way handshake when the client device re-authenticates to the network. If the network you want to pentest has no connected client your out of luck!
On Ferns home screen the networks being detected will start populating next to the WiFi WEP or WiFi WPA buttons. (I have been seeing less and less WEP enabled networks, so that is a good thing!)
Clicking on the WiFi WEP or WiFi WPA button will bring up the Attack screen and the top pane will list the networks found. Select the AP to crack, but before clicking the Attack button to the right let’s go over a couple of settings.
I will use the Regular Attack option, but there is a WPS Attack option and I believe Fern uses the Reaver utility to launch the WPS attack. You can read more about Reaver by clicking here.
Common.txt is the wordlist that comes with the Fern program, but any wordlist you download or have created on your own can be used by hitting the Browse button and pointing Fern to the alternative wordlist file.
With the Regular Attack and the wordlist selected hit the Attack button.
Fern will start the attack and on the left side of the screen the attack steps will turn yellow as Fern works through the various steps. The most important step is capturing the 4-way handshake and Fern will open an aireplay-ng Terminal window showing the progress of deauthentication (if XTerms is checked in the preferences) of the connected client.
It may take several attempts to deauth a client and capture the 4-way handshake.
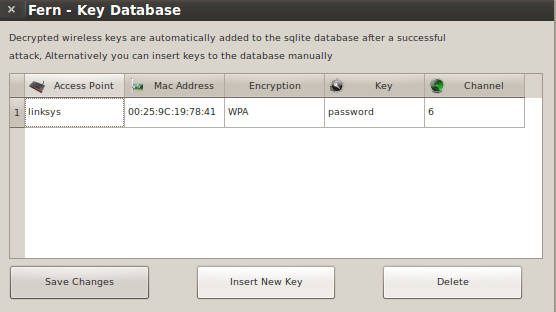
Once Fern has captured the handshake it will start the bruteforce attack. Viola! If the WPA key is in the wordlist being used it will display the found key in Red.
As I mentioned I setup a passphrase I knew would be found quickly, and from start to finish this attack took under 4 minutes!
Back on the Fern main screen is a Key Database button and it now shows one entry.
Clicking the Key Database button will display the found keys.
Conclusion
Using a common dictionary word for a WPA or WPA2 passphrase makes it easier to hack with utilities like Fern. The Fern utility is free to download and simple to use, and not everyone is going to use it for legit wireless pentesting purposes.
With possession of the WPA key a person can associate to network and have a gateway to the internet, or they could launch other attacks. For example, with possession of the WPA key the attack could be expanded to include decryption of the data traffic of the legitimate clients on the wireless network.
Thanks for reading and stay wireless secure!













Thanks for the re-post!
where can download this software sir if u don,t mind send me link muhammadali_775@yahoo.com
Here a link to the download site
https://code.google.com/p/fern-wifi-cracker/downloads/list
Which version of fern WiFi cracker are you using ?? I cracked wep but failed on WPA.
I was using version 1.9, you can this blog post on updating the program and a few of the issues I had using Fern. Thanks for the comment!
that lie within the dictionary key is why it is fast
Correct… as I mentioned in the article I used a simple passphrase and was sure it would be found fast.
why it is not supporting in the virtual box
It has been years since I have done any wireless pentesting and used some of these tools… some of these tools can be very temperamental, and a generic message of something is not working does not give me much to go on to provide any assistance. If there is a specific error message or behavior that is happening you can Google that for clues… Google was my best friend in similar instances when I would run into issues!
key is in the dictionary so it is fast …. if pz
Correct… as I mentioned in the article I used a simple passphrase and was sure it would be found fast. Your comments were not deleted, all comments to the blog have to be approved before being posted. Thanks!
i’d like to ask, so what if the password is not in the list does this mean that it cannot be cracked?
Exactly… If the WPA passphrase is not in the word list being used by Fern then it won’t crack it. That is why it is important to not use a common dictionary word or an easily guessed passphrase. Thanks for the question!
Hello.. Speaks a form or solution to form fruit without dictionary… the dictionary does not include the key if not add it or sometimes bring… For example my dictionary is 2 gb but not even achieve even more delayed almost a 1 day
Ok so my next question is how exactly do I create a good and uncommon dictionary word list? Or should I say how do I create a dictionary on the whole?
Great question, and I haven’t created any custom word lists and have just been using the word lists that come with Fern or one of the other utilities in Backtrack. I do believe there is a utility in Backtrack called genpmk that can create WPA hash tables or word lists, but I have not messed with it. This might be a topic I can try to write about in the future, but in the meantime you can Google search and see if anyone else may all ready have instructions on genpmk. Sorry I could not give you a better answer.
ok thanks for the info
download link?
Latest release shows v1.6, from where to download v1.9? I am using Backtrack5r3, its already have v1.6 installed, what’s the difference between both versions?
Hi Syed, When you open the program look in the lower left corner and if any update is available a message and button should be active to download and install the update. Not much difference in versions… the later version addresses bug fixes and helped me with the program locking up or freezing.
Hello Sir I was trying software downlode .but it is not downlode properly plz help me give me Link…Ric
For anyone new to Fern the best place to start is the Google project page. Along with some general info it has install, update, and usage instructions.
https://code.google.com/p/fern-wifi-cracker/
plz give me link for wordlist
Email : navinbisht7@gmail.com
thanks…
There is a large word list available for download from the Hak5 site.
https://forums.hak5.org/index.php?/topic/29308-13gb-44gb-compressed-wpa-wpa2-word-list-982963904-words/
Works very well. I like it more to use the shell commands but may this will change cuz the GUI just looks very nice 😉
Knowing the commands and switches is a good skill to master, but Fern’s point and click GUI is slick and easy to use, which makes it scary when people with lesser skills use it for not so good intentions!
will this work with windows 7 im looking for a program that will work with windows 7 to crack wpa and wep keys
how to creat a word list ??
Kali has a utility called Crunch that can be used to create custom word lists. Here is a link to an article that explains how to use the Crunch utility.
http://null-byte.wonderhowto.com/how-to/hack-like-pro-crack-passwords-part-4-creating-custom-wordlist-with-crunch-0156817/
Hi Sir! Could you tell me please, how much time does Fern WIFI Cracker takes if I bruteforce WPA encryption with WPS flaw in condition of processing power 2.2 Ghz dual cored AMD Turion microprocessor? While I was cracking WPA with dictionary attack on Airocrack-ng it shows 500 words per second. Can I guess same indications on Fern Cracker or is it cracks less combinations because my microprocessor is generating them? Do you have some articles about WPS cracks and How it works on Fern WIFI Cracker?
Fern is a GUI interface and uses the Reaver utility to crack the WPS flaw. I used the Reaver utility and usually run into issues as most APs notice the repeated tries of pins and stop answering the requests. There are settings to control asking a new pin less frequently to trick the AP, but many successful attacks with Reaver take hours, and I look at other attacks before Reaver since I get impatient with Reaver!
I do aal steps but in shows only “active” but not searching any network
Fern and some of the other WiFi tools can be a challenge at times to get to work! I went through a lot of issues with Fern, and the power of Google is your friend to research any issue! It could be anything from your WiFi adapter is not able to do all the functions, or the install may be corrupt, or a config setting may be set wrong. Please post any error messages or more details of your issue and I can try to help diagnose what the issue is.